AWS Certified Developer - Associate Road Map
Official AWS Centification Page
- 参加 AWS 培训课程
- 查看考试指南和样题
- 了解考试涉及的概念并整体了解需要学习哪些内容, AWS Certified Developer – Associate 考试指南 相当于考试大纲, 必看,而且需要反复的看。因为学习过一阵后再来看Guide,会有更深的体会。
- 考试样题用于熟悉题目题型
- 完成自主进度动手实验和备考任务
- 官方qwikLABS 任务提供了一系列动手实验, 提供部分免费实验,但大部分实验所需的积分都需要购买。高性价比的做法是, 注册一个AWS全球账号,使用一年的免费额度来对照着实验手册来进行试验。
- 学习 AWS 白皮书
- 白皮书是纯英文的,而且每个白皮书篇幅都很长,读起来既费时又枯燥。但是有时间还是建议把推荐的几个都看一下。
- 查看 AWS 常见问题
- 官网推荐的FAQ都建议看完,另外DynamoDB FAQ这个必须要看。
- 参加模拟考试
- 20美刀一次,主要目的是为了让人熟悉考试时上机的流程。是否需要因人而异, 特别想先熟悉下考试流程的可以考虑参加一次。我个人觉得没有必要, 因为真实考试时,操作界面一目了然,没有磕磕绊绊的机关,省下20美刀可以去买一份课程。
- 报名考试并获得认证
考试指南
AWS Certified Developer – Associate 考试指南 读三遍,读三遍,读三遍
各个Domain的分数比例如下:
Domain 3 Deployment and Security 中3.2 中最后一句[CIA and AAA models, ingress vs. egress filtering, and which AWS services and features fit]中的CIA和AAA的解释如下:
CIA are the fundamentals of Information Security
- Confidentiality 机密性 (generally encryption)
- Integrity 完整性 (the accuracy of a message or server…i.e. hash value)
- Availability 可用性 (availability of a service)
AAA
- Authentication
- Authorization
- Accounting
视频学习
Acloudguru 中aws-centified-developer-associate视频的学习,大体内容和Centified Solutions Architect-Associate的大同小异,多了DynamoDB的部分
要点摘录
IAM
IAM give
- Centralised control of your AWS account
- Shared Access to your AWS account
- Granular Permissions
- Identity Federation (including Active Directory, Facebook, Linkedin etc)
- Multifactor Authentication
- Provide temporary access for users/devices and services where necessary
- Allows you to set up your own password rotation policy
- Integrates with many different AWS services
- Supports PCI DSS Compliance
IAM consists of the following:
- Users - End Users (think people)
- Groups (A collection of users under one set of permissions. A way to group our users and apply polices to them collectively)
- Roles - You create roles and can then assign them to AWS resources
- Policy Documents - A document that defines one (or more permissions) - IAM Online Policy Generator12345678910{"Version": "2012-10-17","Statement": [{"Effect": "Allow","Action": "*","Resource": "*"}]}
IAM is universal, It does not apply to regions at this time.
- The “root account” is simply the account created when first setup your AWS account. It has complete Admin access.
- New Users have NO permissions when first created.
- New Users are assigned Access Key ID & Secret Access Keys when first created.
- There are not the same as a password, and you cannot use the Access key ID & Secret Access Key to Login in to the console. You can use this to access AWS via the APIs and Command Line however.
- You only get to view these once. If you lose them, you have to regenerate them. So save them in a secure location.
- Always setup Multifactor Authentication on your root account.
- You can create and customise your own password rotation policies.
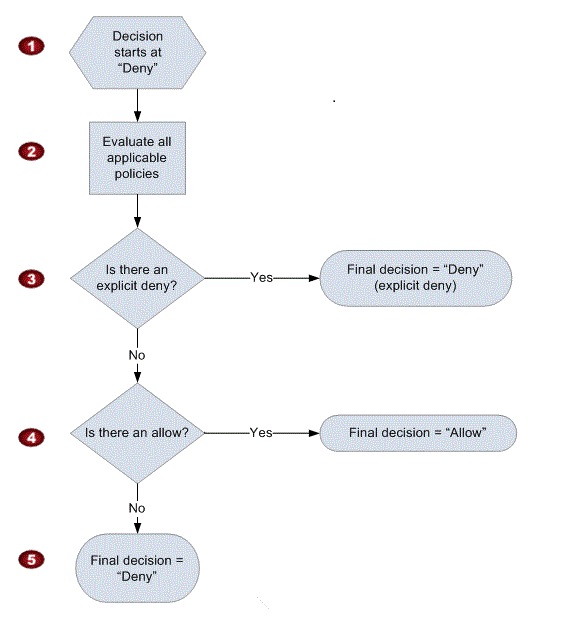
- Determining whether a request is allowed or denied – http://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_evaluation-logic.html
- Start with default deny, and evaluate all applicable policies
- If there is explicit deny, result is deny
- If there is explicit allow, result is allow
STS
- In The Exam
- Develop and Identity Broker to communicate with LDAP and AWS STS
- Identity Broker always authenticates with LDAP first, THEN with AWS STS
- Application then gets temporary access to AWS resource
EC2
know the differences between:
- On Demand - allow you to pay a fixed rate by the hour with no commitment
- Spot - enable you to bi whatever price you want for instance capacity, providing for even greater savings if your applications have flexible start and end times.
- If you terminate the instance, you pay for the hour
- If AWS terminates the spot instance, you get the hour it was terminated in for free.
- Reserved - provide you with a capacity reservation, and offer a significant discount on the hourly charge for an instance. 1 Year or 3 Year Terms
- Dedicated Hosts - Physical EC2 server dedicated for your use. Dedicated Hosts can help you reduce costs by allowing you to use your existing server-bound software licenses.
EC2 Instance Types
| Family | Speciality | Use case |
|---|---|---|
| D2 | Dense Storage | Fileservers/Data Wareshousing/Hadoop |
| R4 | Memory Optimized | Memory Intensive Apps/DBs |
| M4 | General Purpose | Application Servers |
| C4 | Compute Optimized | CPU Intensive Apps/DBs |
| G2 | Graphics Intensive | Video Encoding/3D Application Streaming |
| I2 | High Speed Storage | NoSQL DBs, Data Warehousing etc |
| F1 | Field Programmable Gate Array | Hardware acceleration for your code |
| T2 | Lowest Cost, General Purpose | Web Servers/Small DBs |
| P2 | Graphics/General Purpose GPU | Machine Learning, Bit Coin Mining etc |
| X1 | Memory Optimize | SAP HANA/Apache Spark etc |
How to remember Instance type
- D for Density
- R for RAM
- M - main choice for general purpose apps
- C for Compute
- G - Graphics
- I for IOPS
- F for FPGA
- T cheap general purpose (think T2 micro)
- P - Graphics (think Pics)
- X - Extreme Memory
- DR Mc GIFT PX
EBS Consists of:
- SSD, General Purpose - GP2 - (Up to 10,000 IOPS)
- General purpose, balances both price and performance.
- Ratio of 3 IOPS per GB with up to 10000 IOPS and the ability to burst up to 3000 IOPS for extended periods of time for volumes under 1Gib.
- SSD, Provisioned IOPS - IO1 - (More than 10,000 IOPS)
- Designed for I/O intensive applications such as large relational or NoSQL databases.
- Use if you need more than 10000 IOPS
- Can provision up to 20000 IOPS per volume.
- HDD, Throughput Optimized - ST1 - frequently accessed workloads
- Big data
- Data warehouse
- Log processing
- Cannot be a boot volume
- HDD, Cold - SC1 - less frequently accessed data.
- Lowest Cost Storage for infrequently accessed workloads
- File Server
- Cannot be a boot volume
- HDD, Magnetic - Standard - cheap, infrequently accessed storage
- Lowest cost per gigabyte of all EBS volume types that is bootable. Magnetic volumes are ideal for workloads where data is accessed infrequently, and applications where the lowest storage cost is important.
- You cannot mount 1 EBS volume to multiple EC2 instances, instead use EFS.
- SSD, General Purpose - GP2 - (Up to 10,000 IOPS)
EC2 Lab Exam Tips
- Termination Protection is turned off by default, you must turn it on.
- On an EBS-backed instance, the default action is for the root EBS volume to be deleted when the instance is terminated.
- EBS Root Volumes of your DEFAULT AMI’s cannot be encrypted. you need a third party tool(such as bit locker etc) to encrypt the root volume or this can be done when creating AMI’s in the AWS console or using the API.
- Additional volumes can be encrypted.
Upgrading EBS Volume Types
- EBS Volumes can be changed on the fly (except for magnetic standard)
- Best practice to stop the EC2 instance and then change the volume
- You can change volume types by taking a snapshot and then using the snapshot to create a new volume
- If you change a volume on the fly you must wait for 6 hours before making another change
- You can scale EBS Volumes up only
- Volumes must be in the same AZ as the EC2 instances
Security Group
- All Inbound Traffic is Blocked By Default
- All Outbound Traffic is Allowed
- Changes to Security Groups take effect immediately
- You can have any number of EC2 instances within a security group.
- You can have multiple security groups attached to EC2 Instances
- Security Groups are STATEFUL
- If you create an inbound rule allowing traffic in, that traffic is automatically allowed back out again.
- You cannot block specific IP addresses using Security Groups, instead use Network Access Control Lists.
- You can specify allow rules, but not deny rules.
Volumes vs Snapshots
- Volumes exist on EBS
- Virtual Hard Disk
- Snapshots exist on S3
- You can take a snapshot of a volume, this will store that volume on S3.
- Snapshots are point in time copies of Volumes.
- Snapshots are incremental, this means that only the blocks that have changed since your last snapshot are moved to S3.
- If this is your first snapshot, it may take some time to create.
- Volumes exist on EBS
Volumes vs Snapshots - Security
- Snapshots of encrypted volumes are encrypted automatically.
- Volumes restored from encrypted snapshots are encrypted automatically.
- You can share snapshots, but only if they are unencrypted.
- These snapshots can be shared with other AWS accounts of made public.
Snapshots of Root Device Volumes
- To Create a snapshot for Amazon EBS volumes that serve as root devices, you should stop the instance before taking the snapshot.
EBS vs Instance Store
- Instance Store Volumes are sometimes called Ephemeral Storage.
- Instance store volumes cannot be stopped. If the underlying host fails, you will lose your data.
- EBS backed instances can be stopped. You will not lose the data on this instance if it is stopped.
- You can reboot both, you will not lose your data.
- By default, both ROOT volumes will be deleted on termination, however with EBS volumes, you can tell AWS to keep the root device volume.
How can I take a Snapshot of a RAID Array?
- Problem - Take a snapshot, the snapshot excludes data held in the cache by applications and the OS. This tends not to matter on a single volume, however using multiple volumes in a RAID array, this can be a problem due to interdependencies of the array.
- Solution - Take an application consistent snapshot.
- Stop the application from writing to disk.
- Flush all caches to the disk.
- How can we do this?
- Freeze the file system
- Unmount the RAID Array
- Shutting down the associated EC2 instance.
Amazon Machine Images
- AMI’s are regional. You can only launch an AMI from the region in which it is stored. However you can copy AMI’s to other regions using the console, command line or the Amazon EC2 API.
CloudWatch and CloudTrail
- Standard Monitoring = 5 Minutes
- Detailed Monitoring = 1 Minute
- CloudWatch is for performance monitoring
- CloudTrail is for auditing
- CloudWatch
- Dashboards - Creates awesome dashboards to see what is happening with your AWS environment.
- Alarms - Allows you to set Alarms that notify you when particular thresholds are hit.
- Events - CloudWatch Events helps you to respond to state changes in your AWS resources.
- Logs - CloudWatch Logs helps you to aggregate, monitor, and store logs.
EC2 Role
- Roles are more secure than storing your access key and secret access key on individual EC2 instances.
- Roles are easier to manage
- Roles can only be assigned when that EC2 instance is being provisioned.
- Roles are universal, you can use them in any region.
Instance Meta-data
- Used to get information about an instance(such as public ip)
- curl http://169.254.169.254/latest/meta-data/
- No such thing as user-data for an instance
EFS Features
- Supports the Network File System version 4(NFSv4) protocol
- You only pay for the storage you use (no pre-provisioning required)
- Can scale up to the petabytes
- Can support thousands of concurrent NFS connections
- Data is stored across multiple AZ’s within a region
- Read After Write Consistency
- Great use cases for a file server. You can apply both file level and directory level permissions within EFS.
EC2 CLI Command
- aws ec2 describe-instances
- aws ec2 describe-images
- aws ec2 run-instances
- Do not confuse start-instances with run-instances
- start-instances starts an stopped instance
- run-instances is used to create a new instance
Lambda
- AWS Lambda is a compute service where you can upload your code and create a Lambda function. AWS Lambda takes care of provisioning and managing the servers that you use to run the code. You don’t have to worry about operating systems, patching, scaling, etc. You can use Lambda in the following ways.
- As an event-driven compute service where AWS Lambda runs your code in response to events. These events could be changes to data in an Amazon S3 bucket or an Amazon DynamoDB table.
- As a compute service to run your code in response to HTTP requests using Amazon API Gateway or API calls made using AWS SDKs.
- Language supported
- Node.js
- Java
- Python
- C#
- Lambda Priced
- Number of requests
- First 1 million requests are free. $0.20 per 1 million requests thereafter.
- Duration
- Duration is calculated from the time you code begins executing until it returns or otherwise terminates, rounded up to the nearest 100ms. The price depends on the amount of memory you allocate to your function. You are charged $0.00001667 for every GB-second used.
- Number of requests
- Why is Lambda Cool
- No Servers!
- Continuous Scaling
- Super super super cheap!
- The default timeout of Lambda Function is 3 second, maximum time is 300 second (5 mins), minimum time is 1 second.
- Lambda code(and any dependent libraries) as a Zip and upload to console, Uploads must be no larger than 50MB(compressed).
- Compute resource : You can set your memory in 64MB increments from 128MB to 1.5GB
- AWS Lambda is a compute service where you can upload your code and create a Lambda function. AWS Lambda takes care of provisioning and managing the servers that you use to run the code. You don’t have to worry about operating systems, patching, scaling, etc. You can use Lambda in the following ways.
Elastic Load Balancers
- Instances monitored by ELB are reported as:
- InService
- OutOfService
- Health Checks check the instance health by talking to it
- Have their own DNS name. You are never given an IP address.
- Classic Load Balancer FAQ
- Instances monitored by ELB are reported as:
SDK Tips
- Available SDK
- https://aws.amazon.com/tools/
- Android, iOS, JavaScript(Browser)
- Java
- .Net
- Node.js
- PHP
- Python
- Ruby
- Go
- C++
- Default Region - US-EAST-1
- Some have default regions(Java)
- Some do not (Node.js)
- Available SDK
S3
Exam Tips
- Remember that S3 is Object based i.e. allows you to upload files.
- File can be from 0 Bytes to 5TB.
- There is unlimited storage.
- Files are stored in Buckets.
- S3 is a universal namespace, that is, names must be unique globally.
- https://s3-eu-west-1.amazonaws.com/acloudguru
- Read after Write consistency for PUTS of new Objects
- Eventual Consistency for overwrite PUTS and DELETS (can take some time to propagate)
- Object based storage only ( for files)
- Not suitable to install an operating system on.
- You can insert a presigned url into a webpage to download private data directly from S3.
S3 object consist of:
- Key (This is simply the name of the object)
- Value (This is simply the data and is made up of a sequence of bytes)
- Version ID (Important for versioning)
- Metadata (Data about the data you are storing)
- Subresources
- Access control lists
- Torrent
S3 The Basics
- Built for 99.99 availability for the S3 platform.
- Amazon Guarantee 99.9% availability
- Amazon Guarantees 99.999999999% durability for S3 information. ( Remember 11x9’s)
- Tiered Storage Available
- Lifecycle Management
- Versioning
- Encryption
- Secure your data using Access Control Lists and Bucket Policies
S3 Storage Classes/Tiers
- S3 (durable, immediately available, frequently accessed)
- 99.99% availability, 99.999999999% durability, stored redundantly across multiple devices in multiple facilities and is designed to sustain the loss of 2 facilities concurrently.
- S3 - IA (durable, immediately available, infrequently accessed)
- For data that is accessed less frequently, but requires rapid access when needed. Lower fee than S3, but you are charged a retrieval fee.
- S3 - Reduced Redundancy Storage (data that is easily reproducible, such as thumb nails etc).
- Designed to provide 99.99% durability and 99.99% availability of objects over a given year.
- Glacier - Archived data, where you can wait 3 -5 hours before accessing.
- S3 Storage Tier
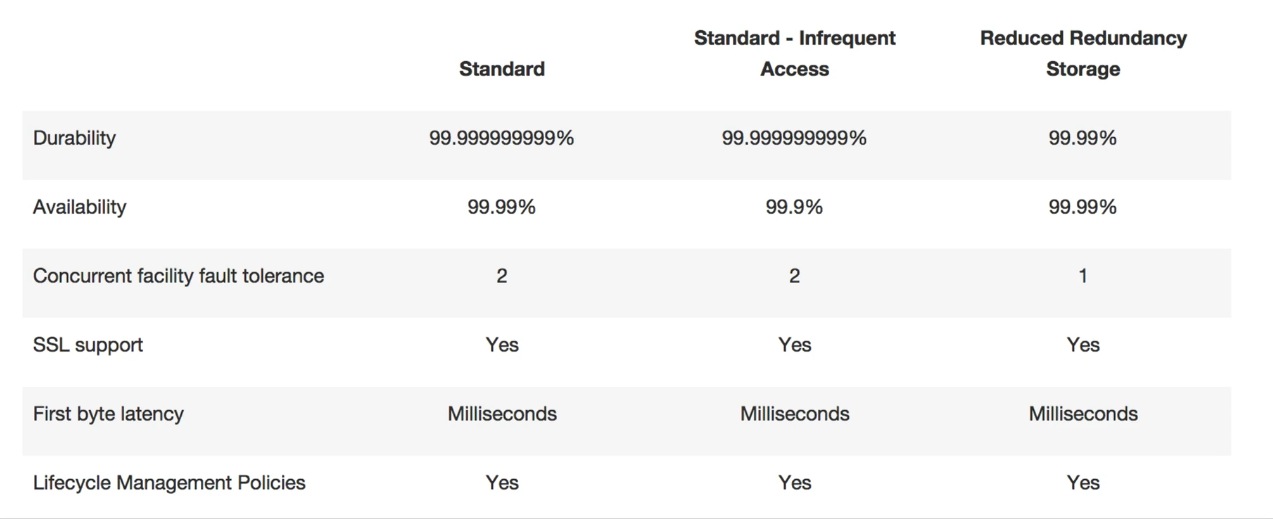
- S3 vs Glacier
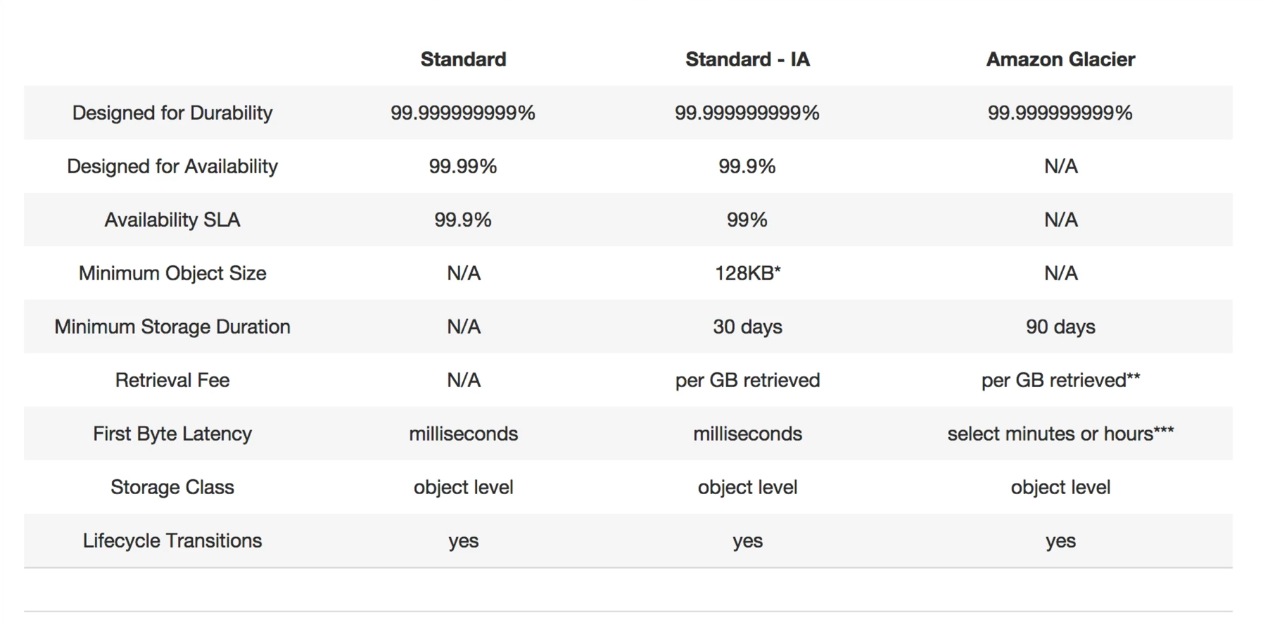
- S3 (durable, immediately available, frequently accessed)
S3 Charges
- Storage
- Requests
- Storage Management Pricing
- Data Transfer Pricing
- Transfer Acceleration
S3 - Versioning
- Stores all versions of an object (including all writes and even if you delete an object)
- Great backup tool.
- Once enabled, Versioning cannot be disabled, only suspended.
- Integrates with Lifecycle rules.
- Versioning’s MFA Delete capability, which uses multi-factor authentication, can be used to provide an additional layer of security.
- Cross Region Replication, requires versioning enabled on the source bucket.
- Any objects uploaded prior to versioning will have the version ID as NULL
Cross Region Replication
- Versioning must be enabled on both the source and destination buckets.
- Regions must be unique.
- Files in an existing bucket are not replicated automatically. All subsequent updated files will be replicated automatically.
- You cannot replicate to multiple buckets of use daisy chaining (at this time).
- When delete object, the delete markers are replicated.
- Deleting individual versions or delete markers will not be replicated.
Lifecycle Management
- Can be used in conjunction with versioning.
- Can be applied to current versions and previous versions.
- Following actions can now be done:
- Transition to the Standard - Infrequent Access Storage Class(128Kb and 30 days after the creation date).
- Archive to the Glacier Storage Class (30 days after IA, if relevant)
- Permanently Delete
CloudFront
- Edge Location - This is the location where content will be cached. This is separate to an AWS Region/AZ
- Origin - This is the origin of all the files that the CDN will distribute. This can be either an S3 Bucket, an EC2 Instance, an Elastic Load Balancer or Route53.
- Distribution - This is the name given the CDN which consists of a collection of Edge Locations.
- Web Distribution - Typically used for Websites.
- RTMP - Used for Media Streaming.
- Edge locations are not just READ only, you can write to them too. (ie put an object on to them)
- Objects are cached for the life of the TTL (Time To Live)
- You can clear cached objects, but you will be charged.
- Restrict viewer access by signed URL or Signed Cookies
- Restrict content based on geo location(whitelist and blacklist)
Securing your buckets
- By default, all newly created buckets are PRIVATE
- You can setup access control to your buckets using:
- Bucket Policies
- Access Control Lists
- S3 buckets can be configured to create access logs which log all requests made to the S3 bucket. This can be done to another bucket.
Encryption
- In Transit:
- SSL/TLS
- At Rest
- Server Side Encryption
- S3 Managed Keys - SSE-S3
- AWS Key Management Service, Managed Keys - SSE-KMS
- Server Side Encryption With Customer Provided Keys - SSE-C
- Client Side Encryption
- Server Side Encryption
- In Transit:
Storage Gateway
- File Gateway - For flat files, stored directly on S3.
- NFS
- Unlimited amount of storage. However maximal file size is 5TB.
- Volume Gateway
- Stored Volumes - Entire Dataset is stored on site and is asynchronously backed up to S3.
- iSCSI based block storage
- Each Volume can store up to 16TB in Size.
- 32 Volumes supported. 512TB of data can be stored (32*16)
- Cached Volumes - Entire Dataset is stored on S3 and the most frequently accessed data is cache on site.
- iSCSI based block storage
- Each Volume can store up to 32TB in Size.
- 32 Volumes supported. 1PB of data can be stored(32*32)
- Stored Volumes - Entire Dataset is stored on site and is asynchronously backed up to S3.
- Gateway Virtual Tape Library (VTL)
- Used for backup and uses popular backup applications like NetBackup, Backup Exec, Veam etc
- iSCSI based virtual tape solution
- Virtual Tape Library (S3) 1500 virtual tapes (1PB)
- Virtual Tape Shelf (Glacier) unlimited tapes.
- Used for backup and uses popular backup applications like NetBackup, Backup Exec, Veam etc
- File Gateway - For flat files, stored directly on S3.
Storage Gateway - General Facts
- Can be deployed on-premise, or as an EC2 instance.
- Can schedule snapshots.
- You can use Storage Gateway with Direct Connect.
- You can implement bandwidth throttling.
- On-Premise needs with either Vmware’s ESXi or Hyper-V.
- Hardware Requirements:
- 4 or 8vCPUs
- 7.5 GB of RAM
- 75 GB for installation of VM image and system data
Storage Gateway - Storage Requirements
- For gateway-cached volume configuration, you will need storage for the local cache and an upload buffer.
- For gateway-stored volume configuration, you will need storage for your entire dataset and an upload buffer. Gateway-stored volumes can range from 1GiB to 1 TB. Each gateway configured for gateway-stored volumes can support up to 12 volumes and a total volume storage of 16TB.
- For gateway-VTL configuration, you will need storage for the local cache and an upload buffer.
Storage Gateway - Networking Requirements
- Open port 443 on your firewalls.
- Internally, you will need to allow port 80 (activation only), port 3260 (by local systems to connect to iSCSI targets exposed by the gateway) and port UDP 53 (DNS)
Storage Gateway - Encryption
- Data in transit is secured using SSL
- Data at rest can be encrypted using AES-256
Gateway-Cached and Gateway-Stored Volumes
- You can take point-in-time, incremental snapshots of your volume and store them in Amazon S3 in the form of Amazon EBS snapshots.
- Snapshots can be initiated on a scheduled or ad-hoc basis.
- Gateway Stored Snapshots
- If your volume data is stored on-premises, snapshots provide durable, off-site backups in Amazon S3.
- You can create a new Gateway-Stored volume from a snapshot in the event you need to recover a backup.
- You can also use a snapshot of your Gateway-Stored volume as the starting point for a new Amazon EBS volume which you can then attach to an Amazon EC2 instance.
- Gateway Cached Snapshots
- Snapshots can be used to preserve versions of your data, allowing you to revert to a prior version when required or to repurpose a point-in-time version as a new Gateway-Cached volume.
Gateway-Virtual Tape Library Retrieval
The virtual tape containing your data must be stored in a Virtual Tape Library before it can be accessed. Access to virtual tapes in your Virtual Tape Library is instantaneous.If the virtual tape containing your data is in your Virtual Tape Shelf, you must first retrieve the virtual tape from your Virtual Tape Shelf. It takes about 24 Hours for the retrieved virtual tape to be available in the selected Virtual Tape Library.
Gateway-Virtual Tape Library Supports
- Symantec NetBackup version 7.x
- Symantec Backup Exec 2012
- Symantec Backup Exec 2014
- Symantec Backup Exec 15
- Microsoft System Center 2012 R2 Data Protection Manager
- Veeam Backup & Replication V7
- Veeam Backup & Replication V8
- Dell NetVault Backup 10.0
Storage Gateway Exam Tips
- Know the four different Storage Gateway Types:
- File Gateway
- Volume Gateway
- Cached - OLD NAME (Gateway-Cached Volumes)
- Stored - OLD NAME (Gateway-Stored Volumes)
- Tape Gateway - OLD NAME (Gateway-Virtual Tape Library)
- Remember that access to virtual tapes in your virtual tape library are instantaneous. If your tape is in the virtual tape shelf(glacier) it can take 24 hours to get back to your virtual tape library.
- Encrypted using SSL for transit and is encrypted at rest in Amazon S3 using AES-256.
- Gateway-Stored Volumes - stores data as Amazon EBS Snapshots in S3.
- Snapshot can be scheduled.
- Bandwidth can be throttled (good for remote sites)
- You need a storage gateway in each site if using multiple locations.
- Know the four different Storage Gateway Types:
Snowball
- Types
- Snowball
- Snowball Edge
- Snowmobile
- Understand what Snowball is
- Understand what Import Export is
- Snowball Can
- Import to S3
- Export from S3
- Types
Import/Export
- Import/Export Disk
- Import to S3, EBS, Glacier
- export from S3
- Import/Export Snowball
- Import to S3
- Export to S3
- Import/Export Disk
S3 Transfer Acceleration
- You can speed up transfers to S3 using S3 transfer acceleration. This costs extra, and has the greatest impact on people who are in for away location.
S3 static Websites
- You can use S3 to host static websites
- Serverless
- Very cheap, scales automatically.
- STATIC only, cannot host dynamic sites.
- Website url example: http://examplebucket.s3-website-us-west-2.amazonaws.com/
S3 CORS
- Cross Origin Resource Sharing
- Need to enable it on the resources bucket and state the URL for the origin that will be calling the bucket.
- http://mybucketname.s3-website.en-west-2.amazonaws.com
- https://s3.eu-west-2.amazonaws.com/mybucketname
S3 multipart upload advantages
- Improved throughput - You can upload parts in parallel to improve throughput.
- Quick recovery from any network issues - Smaller part size minimizes the impact of restarting a failed upload due to a network error.
- Pause and resume object uploads - You can upload object parts over time. Once you initiate a multipart upload there is no expiry; you must explicitly complete or abort the multipart upload.
- Begin an upload before you know the final object size - You can upload an object as you are creating it.
Last Few Tips
- Write to S3 - HTTP 200 code for a successful write.
- You can load files to S3 much faster by enabling multipart upload.
- Read the S3 FAQ before taking the exam. It comes up A LOT!
- S3 bucket name rules
- Bucket names must be at least 3 and no more than 63 characters long
- Bucket names must be a series of one or more labels. Adjacent labels are separated by a single period (.). Bucket names can contain lowercase letters, numbers, and hyphens. Each label must start and end with a lowercase letter or a number (可以有多个lable,每个lable使用.分割,每个lable中只能包含小写字母,数字和连字符-, lable首尾必须要是小写字母或者数字)
- Bucket names must not be formatted as an IP address (e.g., 192.168.5.4).
- When using virtual hosted–style buckets with SSL, the SSL wildcard certificate only matches buckets that do not contain periods. To work around this, use HTTP or write your own certificate verification logic. We recommend that you do not use periods (“.”) in bucket names.
Database
Database component
- Database
- Tables
- Row
- Fields(Columns)
RDS Types
- SQL Server
- Oracle
- MySQL Server
- PostgreSQL
- Aurora
- MariaDB
Non Relational Databases
- Database
- Collection = Table
- Document = Row
- Key Value Pairs = Fields
- Database
Data Warehousing
- Used for business intelligence. Tools like Cognos, Jaspersoft, SQL Server Reporting Services, Oracle Hyperion, SAP NetWeaver.
- Used to pull in very large and complex data sets. Usually used by management to do queries on data ( such as current performance vs targets etc)
OLTP vs OLAP
- Online Transaction Processing (OLTP) differs from Online Analytics Processing (OLAP) in terms of the types of queries run.
- OLTP Example:
Order number 2120212
Pulls up a row of data such as Name, Date, Address to Deliver to, Delivery Status etc. OLAP transaction Example:
Net profit for EMEA and Pacific for the Digital Radio Product.
Pulls in large numbers of recordsSum of Radios Sold in EMEA
Sum of Radios Sold in Pacific
Unit Cost of Radio in each region
Sales price of each radio
Sales price - unit cost.Data Warehousing databases use different type of architecture both from a database perspective and infrastructure layer.
Elasticache
- Elastic Cache is a web service that makes it easy to deploy, operate, and scale an in-memory cache in the cloud. The service improves the performance of web applications by allowing you to retrieve information from fast, managed, in-memory caches, instead of relying entirely on slower disk-based databases.
- ElastiCache supports two open-source in-memory caching engines:
- Memcached
- Redis
DMS
- Announced at re:Invent 2015, DMS stands for Database Migration Service. Allows you to migrate your production database to AWS. Once the migration has started, AWS manages all the complexities of the migration process like data type transformation, compression, and parallel transfer ( for faster data transfer) while ensuring that data changes to the source database that occur during the migration process are automatically replicated to the target.
- AWS schema conversion tool automatically converts the source database schema and a majority of the custom code, including views, stored procedures, and functions, to a format compatible with the target database.
Database Summary
- RDS -OLTP
- SQL
- MySQL
- PostgreSQL
- Oracle
- Aurora
- MariaDB
- DynamoDB - No SQL
- Redshift - OLAP
- Elasticache - In Memory Caching.
- Memcached
- Redis
- DMS
- RDS -OLTP
DynamoDB
- Quick Facts about DynameDB
- Stored on SSD Storage
- Spread Across 3 geographically distinct data centers
- Eventual Consistent Reads (Default)
- Consistency across all copies of data is usually reached within a second. Repeating a read after a short time should return the updated data. (Best Read Performance)
- Strongly Consistent Reads
- A strongly consistent read returns a result that reflects all writes that received a successful response prior to the read.
The Basic
- Tables
- Items ( Think a row of data in table)
- Attributes (Think of a column of data in a table)
Pricing
- Provisioned Throughput Capacity
- Write Throughput $0.0065 per hour for every 10 units
- Read Throughput $0.0065 per hour for every 50 units
- First 25 GB stored per month is free
- Storage costs of $0.25 GB per month there after.
- Provisioned Throughput Capacity
Primary Keys
- Two Types of Primary Keys Available
- Single Attribute (think unique ID)
- Partition Key (Hash Key) composed of one attribute.
- Composite (think unique ID and a data range)
- Partition Key & Sort Key (Hash & Range) composed of two attributes.
- Single Attribute (think unique ID)
- Partition Key and Sort Key
- DynamoDB uses the partition key’s value as input to an internal hash function. The output from the hash function determines the partition (this is simply the physical location in which the data is stored)
- Two items can have the same partition key, but they must have a different sort key.
- All items with the same partition key are stored together, in sorted order by sort key value.
- Two Types of Primary Keys Available
DynamoDB - Indexes
- Local Secondary Index
- Has the SAME Partition key, different sort key.
- Can ONLY be created when creating a table. They cannot be removed or modified later.
- Global Secondary Index
- Has DIFFERENT Partition key and different sort key.
- Can be created at table creation or added LATER.
- Local Secondary Index
DynamoDB Streams
Used to capture any kind of modification of the DynamoDB tables.- If a new item is added to the table, the stream captures an image of the entire item, including all of its attributes.
- If an item is updated, the stream captures the “before” and “after” image of any attributes that were modified in the item.
- If an item is deleted from the table, the stream captures an image of the entire item before it was deleted
Query & Scans
- Query
- A Query operation finds items in a table using only primary key attribute values. You must provide a partition key attribute name and a distinct value to search for.
- You can optionally provide a sort key attribute name and value, and use a comparison operator to refine the search results.
- A Scan operation examines every item in the table. By default, a Scan returns all of the data attributes for every item; however, you can use the ProjectionExpression parameter so that the Scan only returns some of the attributes, rather than all of them.
- Query results are always sorted by the sort key. If the data type of the sort key is a number, the results are returned in numeric order; otherwise, the results are returned in order of ASCII character code values. By default, the sort order is ascending. To reverse the order, set the ScanIndexForward parameter to false.
- By Default is eventually consistent but can be changed to be strongly consistent.
- Scan
- A Scan operation examines every item in the table. By default, a Scan returns all of the data attributes for every item; however, you can use the ProjectionExpression parameter so that the Scan only returns some of the attributes, rather than all of them.
- Try to use a query operation over a Scan operation as it is more efficient.
- Query
DynamoDB Provisioned Throughput
- One read capacity unit represents one strongly consistent read per second, or two eventually consistent reads per second, for an item up to 4 KB in size
- One write capacity unit represents one write per second for an item up to 1 KB in size
- 400 HTTP Status Code - ProvisionedThroughputExceededException indicated You exceeded your maximum allowed provisioned throughput for a table or for one or more global secondary indexes.
- Example
Step taken to authenticate
- User Authenticates with ID provider (such as Facebook)
- They are passed a Token by their ID provider.
- Your code calls AssumeRoleWithWebIdentity API and provides the providers token and specifies the ARN for the IAM Role
- App can now access Dynamodb from between 15 minutes to 1 hour (default is 1 hour)
Conditional Writes
IF item = $10 then update to $12- The conditional writes are idempotent
- You can send the same conditional write request multiple times, but it will have no further effect on the item after the first time DynamoDB performs the specified update.
Atomic Counters
- DynamoDB supports atomic counters
- use the UpdateItem operation to increment or decrement the value of an existing attribute without interfering with other write requests.
- All write requests are applied in the order in which they were received
Batch Operations
If you application needs to read multiple items, you can use the BatchGetItem API. A single BatchGetItem request can retrieve up to 16 MB of data, which can contain as many as 100 items. In addition, a single BatchGetItem request can retrieve items from multiple tables.DynamoDB的操作
- DynamoDB的插入操作
- PutItem
- BatchWriteItem (记住并没有BatchPutItem这种操作)
- DynamoDB的检索操作
- GetItem
- BatchGetItem
- Query API
- DynamoDB的插入操作
Dynamodb limit
- maximum 5 local secondary index per table
- maximum 5 global secondary index per table
- default provision throughput (Account can increase them by contacting AWS)
- US East (N. Virginia) Region
- Per table – 40,000 read capacity units and 40,000 write capacity units
- Per account – 80,000 read capacity units and 80,000 write capacity units
- All Other Regions
- Per table – 10,000 read capacity units and 10,000 write capacity units
- Per account – 20,000 read capacity units and 20,000 write capacity units
- US East (N. Virginia) Region
- No table size limit
- There is an initial limit of 256 tables per region.
- Maximum item size is 400KB(包括属性名称和属性值)
- No limit on the number of attributes of a item, but the size of item can’t exceed 400KB
- BatchGetItem - A single BatchGetItem operation can retrieve a maximum of 100 items. The total size of all the items retrieved cannot exceed 16 MB
- Query - The result set from a Query is limited to 1 MB per call
- Scan - The result set from a Scan is limited to 1 MB per call
- The smallest Reserved Capacity offering is 100 Capacity units(reads or writes)
Read The FAQ!!!
SQS
- SQS usage example
- Asynchronously pulls the task messages from the queue
- Retrieves the named file
- Processes the conversion
- Writes the image back to Amazon S3
- Writes a “task complete” message to another queue
- Deletes the original task message
- Checks for more messages in the worker queue
SQS Tips
- Does not offer FIFO
- 12 hours visibility time out
- Amazon SQS is engineered to provide “at least once” delivery of all messages in its queues. Although most of the time each message will be delivered to your application exactly once, you should design your system so that processing a message more than once does not create any errors or inconsistencies.
- 256kb message size now available
- Billed at 64kb “Chunks”
- A 256kb message will be 4*64kb “chunks”
- You can create any number of message queues.
SQS Pricing
- First 1 million Amazon SQS requests per month are free
- $0.05 per 1 million Amazon SQS Requests per month thereafter ($0.00000050 per SQS Request)
- A single request can have from 1 to 10 messages, up to a maximum total payload of 256KB.
- Each 64KB ‘chunk’ of payload is billed as 1 request. For example, a single API call with a 256KB payload will be billed as four requests.
SQS Delivery
- SQS messages can be delivered multiple times and in any order.
SQS Default Visibility Time Out
- Default Visibility Time Out is 30 Seconds
- Maximum Time Out is 12 Hours
- When you receive a message from a queue and begin processing it, you may find the visibility timeout for the queue is insufficient to fully process and delete that message. To give yourself more time to process the message, you can extend its visibility timeout by using the ChangeMessageVisibility action to specify a new timeout value. Amazon SQS restarts the timeout period using the new value.
SQS Long Polling
- SQS long polling is a way to retrieve messages from your SQS queues. While the traditional SQS short polling returns immediately, even if the queue being polled is empty, SQS long polling doesn’t return a response until a message arrives in the queue, or the long poll times out. SQS long polling makes it easy and inexpensive to retrieve messages from your SQS queue as soon as they are available.
- Maximum Long Poll Time Out = 20 seconds
- 队列属性ReceiveMessageWaitTimeSeconds设置为1~20的数字,在队列中启动长轮询
- 单个ReveiveMessge的请求中将WaitTimeSeconds设置为1~20的数字
SQS Fanning Out
- Create an SNS topic first using SNS. Then create and subscribe multiple SQS queues to the SNS topic.
- Now whenever a message is sent to the SNS topic, the message will be fanned out to the SQS queues, i.e. SNS will deliver the message to all the SQS queues that are subscribed to the topic.
SNS
SNS Benefits
- Instantaneous, push-based delivery (no polling)
- Simple APIs and easy integration with applications
- Flexible message delivery over multiple transport protocols
- Inexpensive, pay-as-you-go model with no up-front costs
- Web-based AWS Management Console offers the simplicity of a point-and-click interface
SNS vs SQS
- Both Messaging Services in AWS
- SNS - Push
- SQS - Polls (Pulls)
SNS Pricing
- Users pay $0.50 per 1 million Amazon SNS Requests
- $0.06 per 100,000 Notification deliveries over HTTP
- $0.75 per 100 Notification deliveries over SMS
- $2.00 per 100,000 Notification deliveries over Email
SNS Summary
- Instantaneous, push-bashed delivery (no polling)
- Protocols include:
- HTTP
- HTTPS
- Email-JSON
- Amazon SQS
- Application
- AWS Lambda
- SMS
- Messages can be customized for each protocol
Valid arguments for an SNS Publish request
12345678910111213141516171819202122POST / HTTP/1.1x-amz-sns-message-type: SubscriptionConfirmationx-amz-sns-message-id: 165545c9-2a5c-472c-8df2-7ff2be2b3b1bx-amz-sns-topic-arn: arn:aws:sns:us-west-2:123456789012:MyTopicContent-Length: 1336Content-Type: text/plain; charset=UTF-8Host: myhost.example.comConnection: Keep-AliveUser-Agent: Amazon Simple Notification Service Agent{"Type" : "SubscriptionConfirmation","MessageId" : "165545c9-2a5c-472c-8df2-7ff2be2b3b1b","Token" : "2336412f37fb687f5d51e6e241d09c805a5a57b30d712f794cc5f6a988666d92768dd60a747ba6f3beb71854e285d6ad02428b09ceece29417f1f02d609c582afbacc99c583a916b9981dd2728f4ae6fdb82efd087cc3b7849e05798d2d2785c03b0879594eeac82c01f235d0e717736","TopicArn" : "arn:aws:sns:us-west-2:123456789012:MyTopic","Message" : "You have chosen to subscribe to the topic arn:aws:sns:us-west-2:123456789012:MyTopic.\nTo confirm the subscription, visit the SubscribeURL included in this message.","SubscribeURL" : "https://sns.us-west-2.amazonaws.com/?Action=ConfirmSubscription&TopicArn=arn:aws:sns:us-west-2:123456789012:MyTopic&Token=2336412f37fb687f5d51e6e241d09c805a5a57b30d712f794cc5f6a988666d92768dd60a747ba6f3beb71854e285d6ad02428b09ceece29417f1f02d609c582afbacc99c583a916b9981dd2728f4ae6fdb82efd087cc3b7849e05798d2d2785c03b0879594eeac82c01f235d0e717736","Timestamp" : "2012-04-26T20:45:04.751Z","SignatureVersion" : "1","Signature" : "EXAMPLEpH+DcEwjAPg8O9mY8dReBSwksfg2S7WKQcikcNKWLQjwu6A4VbeS0QHVCkhRS7fUQvi2egU3N858fiTDN6bkkOxYDVrY0Ad8L10Hs3zH81mtnPk5uvvolIC1CXGu43obcgFxeL3khZl8IKvO61GWB6jI9b5+gLPoBc1Q=","SigningCertURL" : "https://sns.us-west-2.amazonaws.com/SimpleNotificationService-f3ecfb7224c7233fe7bb5f59f96de52f.pem"}SNS limit
- Topic names are limited to 256 characters.
- Token included in the confirmation message sent to end-points on a subscription request are valid for 3 days.
SWF
- SWF worker
- Workers are programs that interact with Amazon SWF to get tasks, process received tasks, and return the results.
- SWF Decider
- The Decider is a program that controls the coordination of tasks, i.e. their ordering, concurrency, and scheduling according to the application logic.
- SWF Workers & Deciders
- The workers and the decider can run on cloud infrastructure, such as Amazon EC2, or on machines behind firewalls. Amazon SWF brokers the interactions between workers and the decider. It allows the decider to get consistent views into the progress of tasks and to initiate new tasks in an ongoing manner. At the same time, Amazon SWF stores tasks, assigns them to workers when they are ready, and monitors their progress. It ensures that a task is assigned only once and is never duplicated. Since Amazon SWF maintains the application’s state durably, workers and deciders don’t have to keep track of execution state. They can run independently and scale quickly.
- SWF Domains
- Your workflow and activity types and the workflow execution itself are all scoped to a domain. Domains isolate a set of types, executions, and task lists from others within the same account. You can register a domain by using the AWS Management Console or by using the RegisterDomain action in the Amazon SWF API.
- The parameter are specified in JavaScript Object Notation(JSON) format.
https://swf.us-east-1.amazonaws.com
RetisterDomain
{
“name” : “1234567”,
“description” : “music”,
“workflowExecutionRetentionPeriodInDays” : “60”
}
- Maximum WorkFlow can be 1 year and the value is always measured in seconds.
SWF vs SQS
- Amazon SWF presents a task-oriented API, whereas Amazon SQS offers a message-oriented API.
- Amazon SWF ensures that a task is assigned only once and is never duplicated. With Amazon SQS, you need to handle duplicated messages and may also need to ensure that a message is processed only once.
- Amazon SWF keeps track of all the tasks and events in an application. With Amazon SQS, you need to implement your own application-level tracking especially if your application uses multiple queues.
SWF limit
- maximum number of SWF domains is 100 (includes both registered and deprecated domains)
- Maximum workflow and activity types - 10,000 each per domain (includes both registered and deprecated types)
- Maximum request size is 1 MB per request (including the request header and all other associated request data.)
- Maximum open workflow executions - 100,000 per domain (includes child workflow executions)
- Maximum workflow execution time - 1 year
- You can only have a maximum of 1,000 open activity tasks per workflow execution.
Elastic Beanstalk
- Supported Application
- Java
- .NET
- PHP
- Node.js
- Python
- Ruby
- Go
- Docker
- Its uses ASG, ELB, EC2, RDS, SNS and S3 to provision things.
- Environment Tier - WebServer, Worker
- Preconfigured docker:
- Glassfish
- Python
- Go
- Environment URL - has to be unique
- Console Item
- Dashboard
- Configuration
- Scaling
- Instances(DIRTMCG instance types, key pair)
- Notifications
- Software configuration
- Updates and Deployments
- Health
- Managed Updates
- Networking tier(ELB, VPC)
- Data tier(RDS)
- Logs
- Health
- Monitoring
- Alarms
- Managed Updates
- Events
- Tags
Route53 DNS
- ELB’s do not have pre-defined IPv4 addresses, you resolve to them using a DNS name.
- Understand the difference between an Alias Record and a CNAME
- Given the choice, always choose an Alias Record over a CNAME.
- Remember the different routing policies and their use cases.
- Simple
- Weighted
- Latency
- Failover
- Geolocation
VPC
- Basic Info
- Think of a VPC as a logical datacenter in AWS
- Consists of IGW’s (Or Virtual Private Gateways), Route Tables, Network Access Control Lists, Subnets, Security Groups
- 1 Subnet = 1 Availability Zone
- Security Groups are Stateful, Network Access Control Lists are Stateless.
- Can Peer VPCs both in the same account and with other AWS accounts.
- No Transitive Peering
- Custom VPC network block size has to be between a /16 netmask and /28 netmask.
- What can you do with a VPC
- Launch instances into a subnet of your choosing
- Assign custom IP address ranges in each subnet
- Configure route tables between subnets
- Create internet gateway and attach it to our VPC
- Much better security control over your AWS resources
- Instance security groups
- Subnet network access control lists (ACLS)
Default VPC vs Custom VPC
- Default VPC is user friendly, allowing you to immediately deploy instances
- All Subnets in default VPC have a route out to the internet.
- Each EC2 instance has both a public and private IP address
- If you delete the default VPC the only way to get it back is to contact AWS.
VPC peering
- Allows you to connect one VPC with another via a direct network route using private IP addresses.
- Instances behave as if they were on the same private network
- You can peer VPC’s with other AWS accounts as well as with other VPCs in the same account.
- Peering is in a star configuration, ie 1 central VPC peers with 4 others, NO TRANSITIVE PEERING!!!
Create VPC
- things automatically created
- Route tables
- Network ACLs
- Security Groups
- DHCP options set
- things are not automatically created
- Internet Gateways
- Subnets
- things automatically created
VPC Subnet
- There are 5 IP address reserved in each subnet by AWS, take CIDR block 10.0.0.0/24 as example
- 10.0.0.0 Network address
- 10.0.0.1 Reserved by AWS for the VPC router
- 10.0.0.2 Reserved by AWS for DNS
- 10.0.0.3 Reserved by AWS for future use.
- 10.0.0.255 Network broadcast address, we do not support broadcast in a VPC, therefore we reserve this address.
- There are 5 IP address reserved in each subnet by AWS, take CIDR block 10.0.0.0/24 as example
NAT instances
- When creating a NAT instance, Disable Source/Destination Check on the Instance
- NAT instance must be in a public subnet
- Must have an elastic IP address to work
- There must be a route out of the private subnet to the NAT instance, in order for this to work
- The amount of traffic that NAT instances supports, depends on the instance size. If you are bottlenecking, increase the instance size
- You can create high availability using Autoscaling Groups, multiple subnets in different AZ’s and a script to automate failover
- Behind a Security Group.
NAT Gateways
- Very new
- Preferred by the enterprise
- Scale automatically up to 10Gbps
- No need to patch
- Not associated with security groups
- Automatically assigned a public ip address
- Remember to update your route tables.
- No need to disable Source/Destination Checks.
NAT instances vs NAT Gateways
| Attribute | NAT gateway | NAT instance |
|---|---|---|
| Availability | Highly available. NAT gateways in each Availability Zone are implemented with redundancy. Create a NAT gateway in each Availability Zone to ensure zone-independent architecture. | Use a script to manage failover between instances. |
| Bandwidth | Supports bursts of up to 10Gbps. | Depends on the bandwidth of the instance type. |
| Maintenance | Managed by AWS.You do not need to perform any maintenance. | Managed by you, for example, by installing software updates or operating system patches on the instance. |
| Performance | Software is optimized for handling NAT traffic. | A generic Amazon Linux AMI that’s configured to perform NAT. |
| Cost | Charged depending on the number of NAT gateways you use, duration of usage, and amount of data that you send through the NAT gateways. | Charged depending on the number of NAT instances that you use, duration of usage, and instance type and size. |
| Type and size | Uniform offering; you don’t need to decide on the type or size. | Choose a suitable instance type and size, according to your predicted workload. |
| Public IP addresses | Choose the Elastic IP address to associate with a NAT gateway at creation. | Use an Elastic IP address or a public IP address with a NAT instance. You can change the public IP address at any time by associating a new Elastic IP address with the instance. |
| Private IP addresses | Automatically selected from the subnet’s IP address range when you create the gateway. | Assign a specific private IP address from the subnet’s IP address range when you launch the instance. |
| Security groups | Cannot be associated with a NAT gateway. You can associate security groups with your resources behind the NAT gateway to control inbound and outbound traffic. | Associate with your NAT instance and the resources behind your NAT instance to control inbound and outbound traffic. |
| Network ACLs | Use a network ACL to control the traffic to and from the subnet in which your NAT gateway resides. | Use a network ACL to control the traffic to and from the subnet in which your NAT instance resides. |
| Flow logs | Use flow logs to capture the traffic. | Use flow logs to capture the traffic. |
| Port forwarding | Not supported. | Manually customize the configuration to support port forwarding. |
| Bastion servers | Not supported. | Use as a bastion server. |
| Traffic metrics | Not supported. | View CloudWatch metrics. |
| Timeout behavior | When a connection times out, a NAT gateway returns an RST packet to any resources behind the NAT gateway that attempt to continue the connection (it does not send a FIN packet). | When a connection times out, a NAT instance sends a FIN packet to resources behind the NAT instance to close the connection. |
| IP fragmentation | Supports forwarding of IP fragmented packets for the UDP protocol. Does not support fragmentation for the TCP and ICMP protocols. Fragmented packets for these protocols will get dropped. | Supports reassembly of IP fragmented packets for the UDP, TCP, and ICMP protocols. |
Network ACL’s
- Your VPC automatically comes a default network ACL and by default it allows all outbound and inbound traffic.
- You can create a custom network ACL. By default, each custom network ACL denies all inbound and outbound traffic until you add rules.
- Each subnet in your VPC must be associated with a network ACL. If you don’t explicitly associate a subnet with a network ACL, the subnet is automatically associated with the default network ACL.
- You can associate a network ACL with multiple subnets; however, a subnet can be associated with only one network ACL at a time. When you associate a network ACL with a subnet, the previous association is removed.
- A network ACl contains a numbered list of rules that is evaluated in order, starting with the lowest numbered rule.
- A network ACl has separate inbound and outbound rules, and each rule can either allow or deny traffic.
- Network ACLs are stateless responses to allowed inbound traffic are subject to the rules for outbound traffic (and vice versa)
- Block IP Addresses using network ACL’s not Security Groups
Security Group vs Network ACL
| Security Group | Network ACL |
|---|---|
| operates at the instance level (first layer of defense) | Operates at the subnet level (second layer of defense) |
| Supports allow rules only | Supports allow rules and deny rules |
| Is stateful: Return traffic is automatically allowed, regardless of any rules | Is stateless: Return traffic must be explicitly allowed by rules |
| We evaluate all rules before deciding whether to allow traffic | We process rules in number order when deciding whether to allow traffic |
| Applies to an instance only if someone specifies the security group when launching the instance, or associates the security group with the instance later on | Automatically applies to all instances in the subnets it’s associated with (backup layer of defense, so you don’t have to rely on someone specifying the security group) |
NAT vs Bastions
- A NAT is used to provide internet traffic to EC2 instances in private subnets
- A Bastion is used to securely administer EC2 instance (using SSH or RDP) in private subnets. In Australia we call them jump boxes.
Resilient Architecture
- If you want resiliency, always have 2 public subnets and 2 private subnets. Make sure each subnet is in different availability zones.
- With ELB’s make sure they are in 2 public subnets in 2 different availability zones.
- With Bastion hosts, put them behind an autoscaling group with a minimum size of 2. Use Route53 (either round robin or using a health check) to automatically fail over.
- NAT instances are tricky to make resilient. You need 1 in each public subnet, each with their own public IP address, and you need to write a script to fail between the two. Instead where possible, use NAT gateways.
VPC Flow Logs
- You can monitor network traffic within your custom VPC’s using VPC Flow Logs.
VPC limit
- Currently you can create 200 subnets per VPC by default
CloudFormation
- Use of CFT(CloudFormation Templates), Beanstalk and AutoScaling are free but you pay for the AWS resources that these services create.
- Fn::GetAtt - values that you can use to return result for an AWS created resource or used to display in output
- By Default - rollback everything on error
- Infrastructure as a code, Version controlled, declarative and flexible
- API ListStackResources is used to list all resources that belong to a CloudFormation Stack
You can use intrinsic functions only in specific parts of a template. Currently, you can use intrinsic functions in resource properties, metadata attributes, and update policy attributes.
CloudFormation Basic
- http://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/gettingstarted.templatebasics.html
- Learn about the following about templates:
- Declaring resources and their properties
- Referencing(提取) other resources with the Ref function and resource attributes using the Fn::GetAtt function
- Using parameters to enable users to specify values at stack creation time and using constraints to validate parameter input
- Using mappings to determine conditional values
- Using the Fn::Join function to construct values based on parameters, resource attributes, and other things
- Using output values based to capture information about the stack’s resources.
CloudFormation intrinsic Function
- Fn::Base64
- returns the Base64 representation of the input string. this function is typically used to pass encoded data to Amazon EC2 instances by way of the UserData property.
- JSON Format { “Fn::Base64” : valueToEncode }
- Fn::FindInMap
- returns the value corresponding to keys in a two-level map that is declared in the Mapping section.
- JSON Format { “Fn::FindInMap” : [ “MapName”, “TopLevelKey”, “SecondLevelKey”] }
- Fn::GetAtt
- returns the value of an attribute from a resource in the template
- JSON Format { “Fn::GetAtt” : [ “logicalNameOfResource”, “attributeName” ] }
- Fn::Join
- Fn::Join appends a set of values into a single value, separated by the specified delimiter. If a delimiter is the empty string, the set of values are concatenated with no delimiter.
- JSON Format { “Fn::Join” : [ “delimiter”, [ comma-delimited list of values ] ] }
- JSON example {“Fn::Join” : [ “:”, [ “a”, “b”, “c” ] ]} will returns “a:b:c”
- Fn::Select
- returns a single object from a list of objects by index
- JSON Format { “Fn::Select” : [ index, listOfObjects ] }
- JSON example { “Fn::Select” : [ “1”, [ “apples”, “grapes”, “oranges”, “mangoes” ] ] } will returns “grapes”
- Fn::Split
- To split a string into a list of string values so that you can select an element from the resulting string list.
- JSON Format { “Fn::Split” : [ “delimiter”, “source string” ] }
- JSON example { “Fn::Split” : [ “|” , “a|b|c” ] } will return [“a”, “b”, “c”]
Fn::Sub
- 将输入字符串中的变量替换为您指定的值
- JSON Format { “Fn::Sub” : [ String, { Var1Name: Var1Value, Var2Name: Var2Value } ] }
- JSON example - 将AWS::Region和AWS::StackName替换为实际的值123456"UserData": { "Fn::Base64": { "Fn::Join": ["\n", ["#!/bin/bash -xe","yum update -y aws-cfn-bootstrap",{ "Fn::Sub": "/opt/aws/bin/cfn-init -v --stack ${AWS::StackName} --resource LaunchConfig --configsets wordpress_install --region ${AWS::Region}" },{ "Fn::Sub": "/opt/aws/bin/cfn-signal -e $? --stack ${AWS::StackName} --stack ${AWS::StackName} --resource WebServer --region ${AWS::Region}" }]]}}
Ref
- returns the value of the specified parameter or resource.
- When you specify a parameter’s logical name, it returns the value of the parameter.
- When you specify a resource’s logical name, it returns a value that you can typically use to refer to that resource, such as a physical ID.
- JSON Format { “Ref” : “logicalName” }
- returns the value of the specified parameter or resource.
- Fn::Base64
CloudFormation limit
- You can include up to 60 parameters and 60 outputs in a template.
- There are no limit to the number of templates.
- Each AWS CloudFormation account is limited to a maximum of 200 stacks.
CloudFormation – Ref, Fn::Join, GetAtt, Fn::split, Fn::select and etc function
Doc
DynamoDB Doc
FAQ
- https://amazonaws-china.com/cn/dynamodb/faqs/?nc1=h_ls
- https://amazonaws-china.com/lambda/faqs/
- https://amazonaws-china.com/api-gateway/faqs/
考点
- http://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers.html
- http://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/template-anatomy.html
- Template Sections
- https://aws.amazon.com/security/penetration-testing/
注意点摘录:
- 筛选表达式(–filter-expression)在 Scan 已完成但结果尚未返回时应用。因此,无论是否存在筛选表达式,Scan 都将占用同等数量的读取容量
术语
- scalar data types –> 标量数据类型
- collection data types –> 集合数据类型
- projection –> 投影
- Fine Grained Access Control (FGAC) –> 精细访问控制
- write-through –> 直写
- optimistic – 乐观
外部资料
- 老外心得 https://acloud.guru/forums/aws-certified-developer-associate/discussion/-KUdI5f2LNbi4wvK7v4I/how-to-pass-aws-certified-developer-exam
- 老外心得 https://acloud.guru/forums/aws-certified-developer-associate/discussion/-KPuWHwfTCiCJNsGzAwu/passed
- re:Invent videos. “Deep Dive on Amazon DynamoDB” https://www.youtube.com/watch?v=bCW3lhsJKfw