深挖AWS S3的权限管理(实验篇)
在深挖AWS S3的权限管理 一文中介绍了AWS S3权限管理的三种方法。此处再通过几个实验来看下三种方法的使用方法。
实验前准备
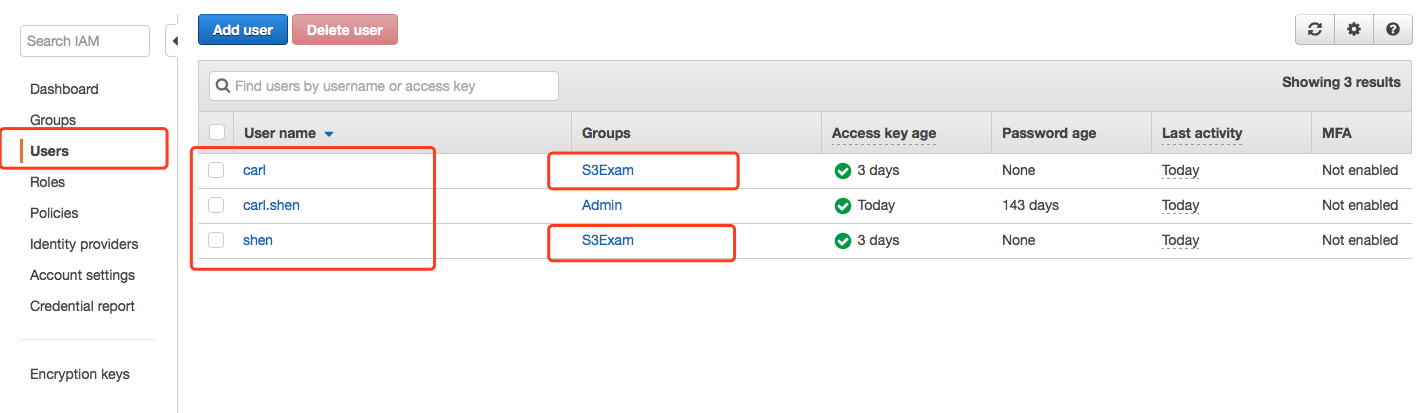
实验用相关账号介绍
- IAM User carl.shen - carl.shen有AdministratorAccess权限,用来上传图片到S3
- IAM User carl - 测试IAM User一号,初始没有任何权限
- IAM User shen - 测试IAM User二号,初始没有任何权限
- IAM Group S3Exam - 用来给IAM User carl和shen统一赋权限
建好三个IAM账号,下载各自的Access key ID和Secret Access Key, 并设置好AWS CLI。AWS CLI多profile的设置方法可以参照 如何在aws cli中使用多个配置文件
建立好IAM Group S3Exam,将carl和shen添加进S3Exam中。
实验用Bucket介绍
- carl-test-at-seoul - 测试Bucket 1,初始没有任何Bucket Policy
- carl-test-at-seoul-2 - 测试Bucket 2,初始没有任何Bucket Policy
工具
- AWS CLI
- Chrome浏览器 - 用来匿名访问S3 Object的url
测试图片
两张测试图片:

实验项目
- 测试Default Deny
- 测试Object ACL public-read
- 测试Bucket Policy Explicit Allow override Default Deny
- 测试Bucket Policy Explicit Deny override Explicit Allow
- 测试Bucket Policy 禁止某个IAM访问
- 测试IAM Policy
- 测试Bucket Policy不能跨Bucket授权
- 测试IAM Policy授权多个Bucket的操作
实验
实验1 – 测试Default Deny
步骤: Bucket carl-test-at-seoul没有Bucket Policy,carl.shen cli传图片进S3,测试chrome和IAM访问
使用AWS CLI用carl.shen账号上传图片
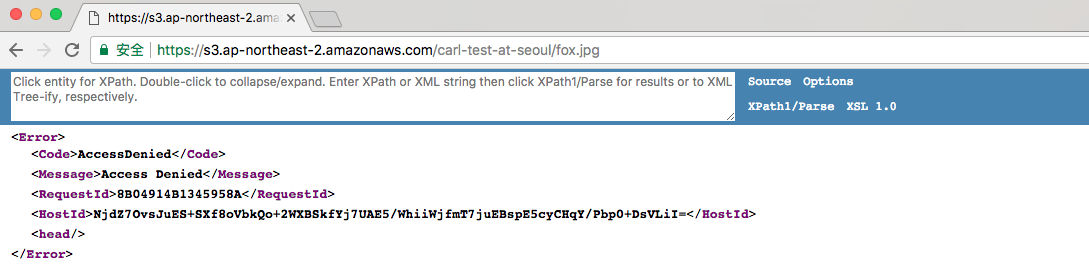
12345$ aws --profile carlshen s3 cp photo_used_for_test/fox.jpg s3://carl-test-at-seoul/upload: photo_used_for_test/fox.jpg to s3://carl-test-at-seoul/fox.jpg$ aws --profile carlshen s3 ls s3://carl-test-at-seoul/2017-12-18 14:49:30 11432 fox.jpg$使用Chrome访问fox.jpg的public url, 会提示AccessDenied, 因为上传到S3的fox.jpg, 默认是access deny的。
同样,IAM User carl和shen也都没有权限获取fox.jpg
12345678# IAM User carl没有访问fox.jpg的权限$ aws --profile carl s3 cp s3://carl-test-at-seoul/fox.jpg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden# IAM User shen没有访问fox.jpg的权限$ aws --profile shen s3 cp s3://carl-test-at-seoul/fox.jpg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden$
实验2 – 测试Object ACL public-read
步骤: Bucket carl-test-at-seoul没有Bucket Policy,carl.shen cli传图片进S3, 设置public-read acl,测试chrome和IAM访问
使用AWS CLI以carl.shen账号上传图片steve.jpeg,并设置图片的Object ACL为public-read
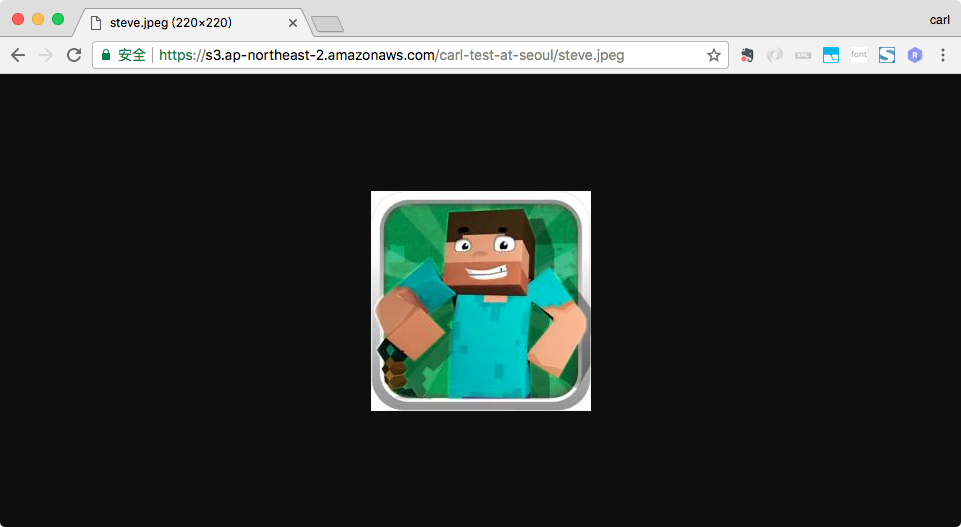
123456$ aws --profile carlshen s3 cp photo_used_for_test/steve.jpeg s3://carl-test-at-seoul/ --acl public-readupload: photo_used_for_test/steve.jpeg to s3://carl-test-at-seoul/steve.jpeg$ aws --profile carlshen s3 ls s3://carl-test-at-seoul/2017-12-18 14:49:30 11432 fox.jpg2017-12-18 15:02:02 9619 steve.jpeg$使用Chrome访问steve.jpeg的public url, steve.jpeg可以被Chrome访问到。因为此时steve.jpeg的Object ACL是public-read,而explicit allow will override the default deny
使用IAM User carl和shen也都可以获取到steve.jpeg
12345678# IAM User carl有权限访问steve.jpeg$ aws --profile carl s3 cp s3://carl-test-at-seoul/steve.jpeg ./download_from_s3/download: s3://carl-test-at-seoul/steve.jpeg to download_from_s3/steve.jpeg# IAM User shen有权限访问steve.jpeg$ aws --profile shen s3 cp s3://carl-test-at-seoul/steve.jpeg ./download_from_s3/download: s3://carl-test-at-seoul/steve.jpeg to download_from_s3/steve.jpeg$
实验3 – 测试Bucket Policy Explicit Allow override Default Deny
步骤: 设置Bucket carl-test-at-seoul的Policy, 设为public to read, 测试chrome和IAM访问
设置Bucket carl-test-at-seoul的Policy,使得carl-test-at-seoul都public to read.
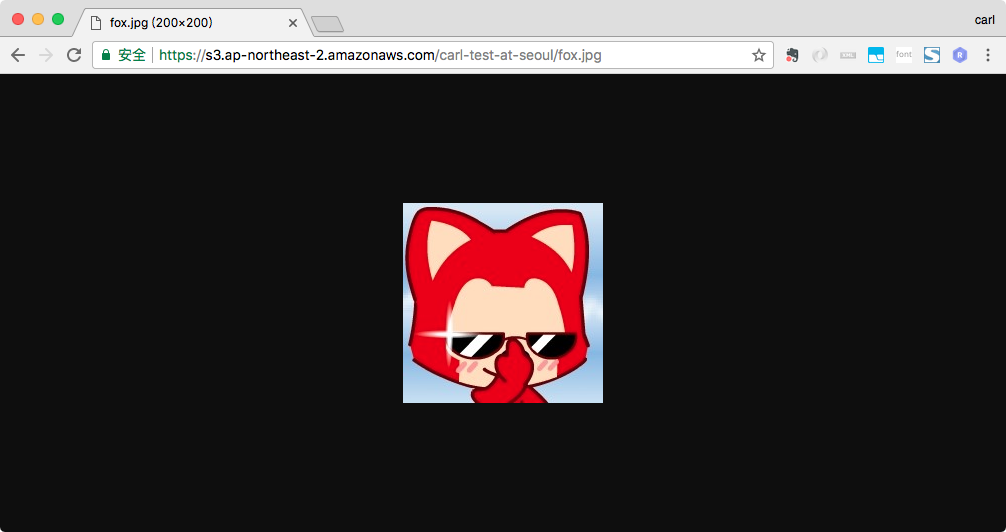
12345678910111213{"Version": "2012-10-17","Id": "Policy1512465896017","Statement": [{"Sid": "Stmt1512465891857","Effect": "Allow","Principal": "*","Action": "s3:GetObject","Resource": "arn:aws:s3:::carl-test-at-seoul/*"}]}使用Chrome访问原先没权限的访问的fox.jpg的url, fox.jpg可以被访问到,因为Bucket Policy的explict allow会覆盖default deny.
此时,carl和shen也可以访问到fox.jpg
12345678# IAM User carl有权限访问fox.jpg$ aws --profile carl s3 cp s3://carl-test-at-seoul/fox.jpg ./download_from_s3/download: s3://carl-test-at-seoul/fox.jpg to download_from_s3/fox.jpg# IAM User shen有权限访问fox.jpg$ aws --profile shen s3 cp s3://carl-test-at-seoul/fox.jpg ./download_from_s3/download: s3://carl-test-at-seoul/fox.jpg to download_from_s3/fox.jpg$
实验4 – 测试Bucket Policy Explicit Deny override Explicit Allow
步骤: Bucket carl-test-at-seoul设置Policy to deny,再测试chrome和IAM访问
修改Bucket carl-test-at-seoul的Policy, Deny s3:GetObject的访问。
12345678910111213{"Version": "2012-10-17","Id": "Policy1512465896017","Statement": [{"Sid": "Stmt1512465891857","Effect": "Deny","Principal": "*","Action": "s3:GetObject","Resource": "arn:aws:s3:::carl-test-at-seoul/*"}]}使用Chrome访问fox.jpg和steve.jpeg, fox.jpg和steve.jpeg都无法被访问。即使steve.jpeg是ACL public-read的,但因为Bucket Policy中显示声明了deny,而exclipit deny会override explicity allow, 所以steve.jpeg也被禁止访问。
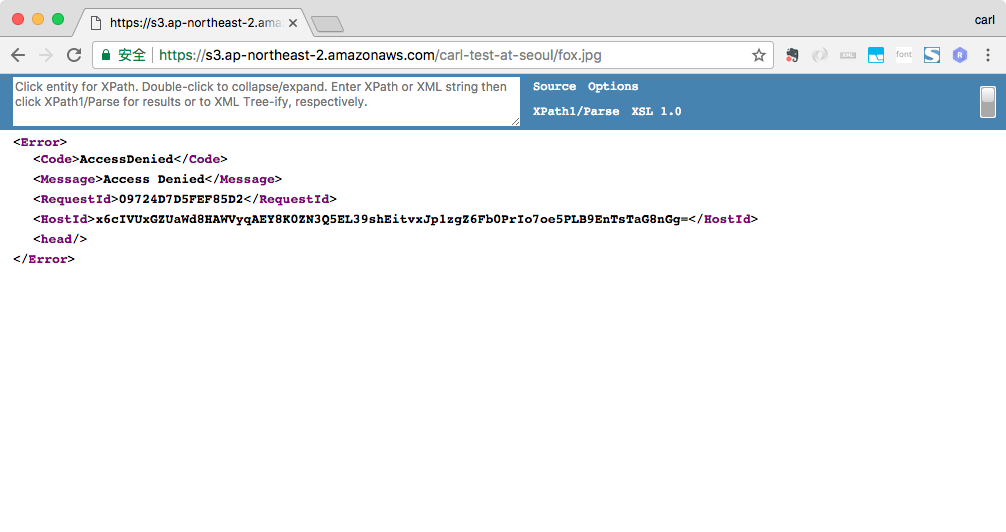
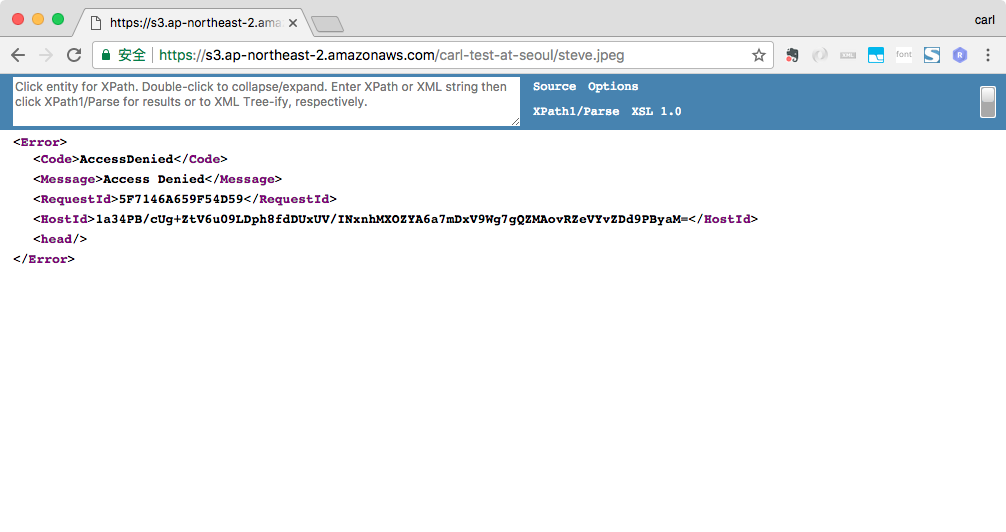
IAM carl和shen也无法访问到fox.jpg和steve.jpeg
123456789101112# IAM User carl没权限访问fox.jpg和steve.jpeg$ aws --profile carl s3 cp s3://carl-test-at-seoul/fox.jpg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden$ aws --profile carl s3 cp s3://carl-test-at-seoul/steve.jpeg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden# IAM User shen没权限访问fox.jpg和steve.jpeg$ aws --profile shen s3 cp s3://carl-test-at-seoul/fox.jpg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden$ aws --profile shen s3 cp s3://carl-test-at-seoul/steve.jpeg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden$
实验5 – 测试Bucket Policy 禁止某个IAM访问
步骤: 修改Bucket Policy为禁止carl访问,此时chrome和shen还是可以访问的。
修改Bucket carl-test-at-seoul的Policy, 禁止IAM User carl的s3:GetObject的操作。
123456789101112131415{"Version": "2012-10-17","Id": "Policy1512465896017","Statement": [{"Sid": "Stmt1512465891857","Effect": "Deny","Principal": {"AWS": "arn:aws:iam::XXXXXXXXXXXX:user/carl"},"Action": "s3:GetObject","Resource": "arn:aws:s3:::carl-test-at-seoul/*"}]}使用Chrome访问fox.jpg和steve.jpeg。Buckt Policy被修改为禁止IAM carl访问Object,但该Policy的实施对象是IAM User carl,所以对Chrome的匿名访问不起作用,因此从Chrome上访问时,带有public-read的steve.jpeg可以访问到,没有public-read ACL的fox.jpg还是无法访问到。
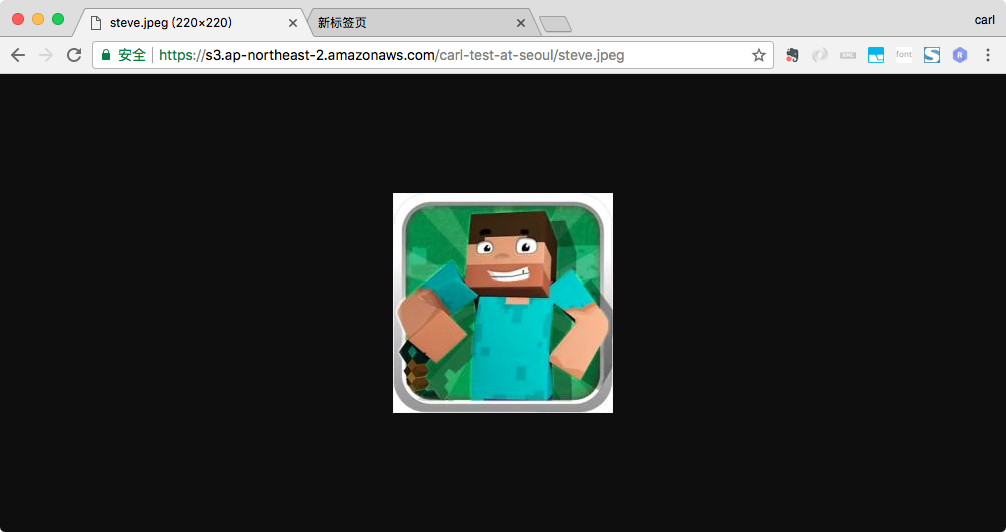
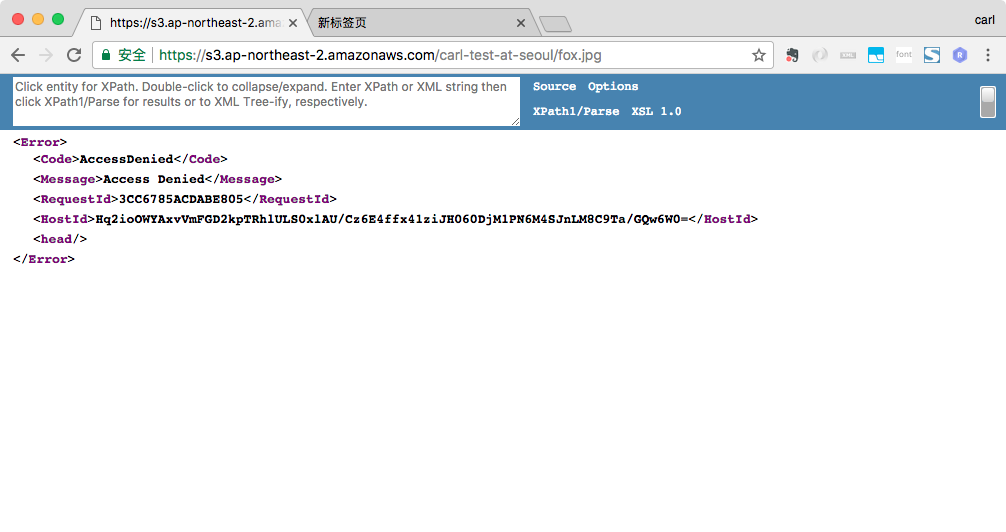
IAM User carl被Bucket Policy禁止访问fox.jpg和steve.jpeg, 而IAM User shen不受Bucket Policy影响,从而可以访问steve.jpeg,但因为没有explicit allow的规则而无法访问fox.jpg
123456789101112# IAM User carl被禁止get carl-test-at-seoul的Object$ aws --profile carl s3 cp s3://carl-test-at-seoul/fox.jpg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden$ aws --profile carl s3 cp s3://carl-test-at-seoul/steve.jpeg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden# IAM User carl不能访问fox.jpg,但能访问steve.jpeg$ aws --profile shen s3 cp s3://carl-test-at-seoul/fox.jpg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden$ aws --profile shen s3 cp s3://carl-test-at-seoul/steve.jpeg ./download_from_s3/download: s3://carl-test-at-seoul/steve.jpeg to download_from_s3/steve.jpeg$
实验6 – 测试IAM Policy
步骤: 修改IAM Group Policy为允许访问carl-test-at-seoul的全部资源,但因为Bucket Policy中是禁止carl访问资源的,因此carl还是无法访问bucket中的内容
将carl和shen所在的Group S3Exam的Policy设为如下,即允许任意S3操作
12345678910111213{"Version": "2012-10-17","Statement": [{"Effect": "Allow","Action": "s3:*","Resource": ["arn:aws:s3:::carl-test-at-seoul","arn:aws:s3:::carl-test-at-seoul/*"]}]}修改S3Exam的Policy后,carl和shen自动就继承了S3Exam的权限
shen可以访问carl-test-at-seoul的全部资源了,包括没有public-read ACL的fox.jpg。carl因为Bucket Policy中还是禁止他访问的,因此还是没有权限获取carl-test-at-seoul中的任意Object
123456789101112# IAM User carl还是没有访问carl-test-at-seoul的权限$ aws --profile carl s3 cp s3://carl-test-at-seoul/fox.jpg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden$ aws --profile carl s3 cp s3://carl-test-at-seoul/steve.jpeg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden# IAM User shen获取了carl-test-at-seoul的全部权限,因此可以访问fox.jpg$ aws --profile shen s3 cp s3://carl-test-at-seoul/fox.jpg ./download_from_s3/download: s3://carl-test-at-seoul/fox.jpg to download_from_s3/fox.jpg$ aws --profile shen s3 cp s3://carl-test-at-seoul/steve.jpeg ./download_from_s3/download: s3://carl-test-at-seoul/steve.jpeg to download_from_s3/steve.jpeg$
实验7 – 测试Bucket Policy不能跨Bucket授权
步骤: Bucket carl-test-at-seoul添加对Bucket carl-test-at-seoul-2的访问,会报错
修改Bucket carl-test-at-seoul的Policy为如下:
12345678910111213{"Version": "2012-10-17","Id": "Policy1512465896017","Statement": [{"Sid": "Stmt1512465891857","Effect": "Deny","Principal": "*","Action": "s3:GetObject","Resource": "arn:aws:s3:::carl-test-at-seoul-2/*"}]}会提示”Error Policy has invalid resource”, 因为无法在当前Bucket的Policy中添加对其他Bucket的访问权限。
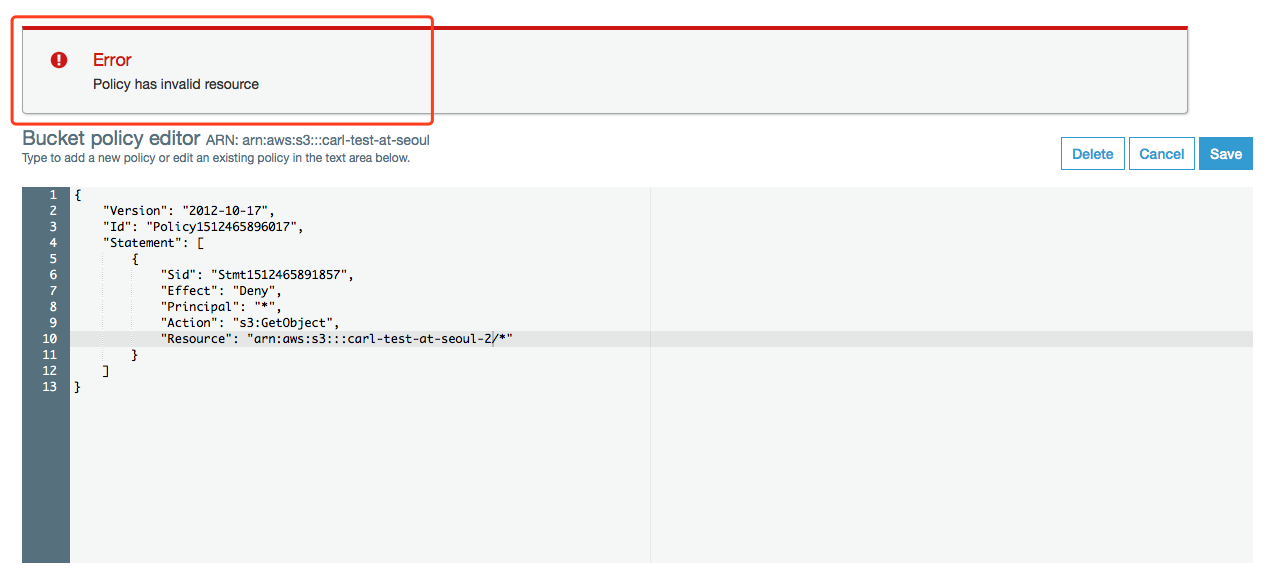
实验8 – 测试IAM Policy授权多个Bucket的操作
步骤: Group Policy中添加对carl-test-at-seoul2的访问,通过carl.shen传文件到carl-test-at-seoul2后,carl和shen能够访问了,但是chrome无法访问,因为IAM Policy, 只能对IAM实体(IAM User, Group, Role)起作用,无法对匿名用户起作用
S3Exam的Policy中只有Bucket carl-test-at-seoul时,carl和shen没有权限访问Bucket carl-test-at-seoul-2的资源。
12345678910111213# 使用carl.shen上传图片到Bucket carl-test-at-seoul-2中$ aws --profile carlshen s3 cp photo_used_for_test/steve.jpeg s3://carl-test-at-seoul-2/upload: photo_used_for_test/steve.jpeg to s3://carl-test-at-seoul-2/steve.jpeg$ aws --profile carlshen s3 ls s3://carl-test-at-seoul-2/2017-12-19 14:15:26 9619 steve.jpeg# IAM User carl 没有权限访问Bucket carl-test-at-seoul-2的资源$ aws --profile carl s3 cp s3://carl-test-at-seoul-2/steve.jpeg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden# IAM User shen 没有权限访问Bucket carl-test-at-seoul-2的资源$ aws --profile shen s3 cp s3://carl-test-at-seoul-2/steve.jpeg ./download_from_s3/fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden$在S3Exam中添加对Bucket carl-test-at-seoul-2的访问权限, 修改后的Bucket Policy如下:
123456789101112131415{"Version": "2012-10-17","Statement": [{"Effect": "Allow","Action": "s3:*","Resource": ["arn:aws:s3:::carl-test-at-seoul","arn:aws:s3:::carl-test-at-seoul/*","arn:aws:s3:::carl-test-at-seoul-2","arn:aws:s3:::carl-test-at-seoul-2/*"]}]}添加权限后,使用Chrome访问Bucket carl-test-at-seoul-2中的steve.jpeg时,无法访问。因为IAM Policy不对匿名访问生效
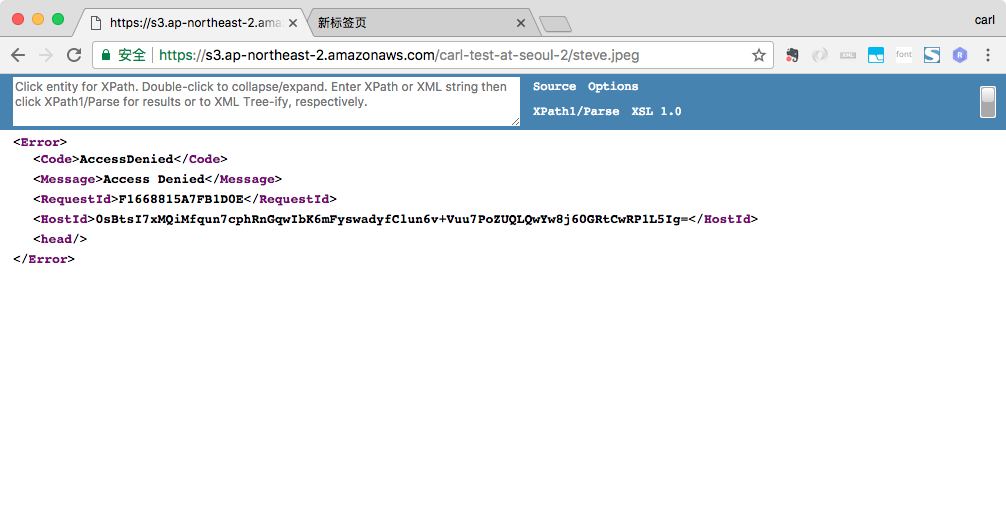
添加权限后,carl和shen就可以访问Bucket carl-test-at-seoul-2的资源了。
1234567# carl可以访问Bucket carl-test-at-seoul-2的资源$ aws --profile carl s3 cp s3://carl-test-at-seoul-2/steve.jpeg ./download_from_s3/download: s3://carl-test-at-seoul-2/steve.jpeg to download_from_s3/steve.jpeg# shen可以访问Bucket carl-test-at-seoul-2的资源$ aws --profile shen s3 cp s3://carl-test-at-seoul-2/steve.jpeg ./download_from_s3/download: s3://carl-test-at-seoul-2/steve.jpeg to download_from_s3/steve.jpeg